
We often talk about malware that appears ready to attack millions of terminals around the world. Following the latest attacks on a global scale, the ciberseguridad It has been gaining more prominence and currently, whenever a harmful element appears, it immediately appears on specialized portals in all regions. As we have previously recalled, software developers must be vigilant.
A few hours ago he was intercepted another object In this case, it could make use of the largest messaging platforms and social networks on the planet to camouflage itself. Below we will tell you more about it and tell you, once again, how it works and also, how to prevent its spread between our terminals. Is it an isolated threat or will its repercussions be greater?
Known malware?
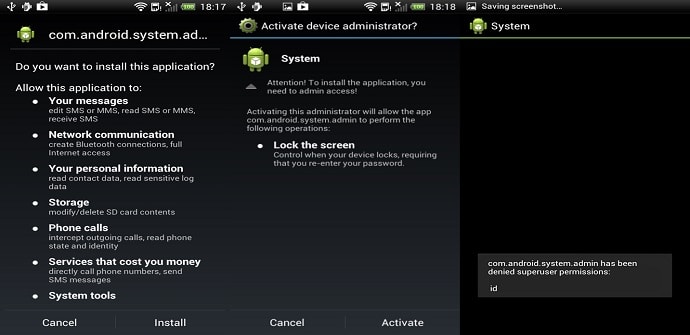
This element, which has been called SpyDealerIt might have been in action for a couple of years. However, in recent months it has been improving and reaching a higher incidence rate. This is what has made him come to the fore recently. According to the company that intercepted him, based in the Californian city of Palo Alto, there would be more than 1.000 variants of this object and would be in an advanced stage of development that would make it more effective.
How It Works
Its mechanics do not differ much from other existing malware. It infiltrates applications, which in this case could be some of the most popular in the world. You then get personal information of users stored in the terminals such as email accounts, addresses and search history. It then infiltrates further until it gains administrator permissions. Among the other tasks that you can perform, we find taking photographs without permission or tracking the location. WhatsApp, Facebook or Telegram could be some of the channels through which it could be transmitted.

How to prevent it?
Everything indicates that this malware would spread through wireless networks. In this case, the most effective measures we can take to avoid being infected are, for example, not accessing public connections and not transmitting any data through them. On the other hand, we add the usual recipes: Use only the most established browsers, exclusively download apps that come from prominent developers and use only home WiFi, or in any case, one that we trust. We leave you more related information about others their that have appeared recently so you can learn more.