
As we have mentioned on other occasions, with the arrival of new terminals, especially those manufactured in China, a series of operating systems have appeared that, despite having all the same base when coming from Android, aim to improve the user experience through a series of added functions as in the cases of Oxygen or Cyanogen.
However, security remains a pending task to be solved for software developers, who constantly have to face serious threats that can compromise the privacy of users through actions such as the theft of data or personal content and that they cannot solve. entirely with new operating system updates. However, we can find some exception like Silent OS present in some terminals such as Nvidia's Blackphone 2 and whose strengths we will discuss below.
Android Product
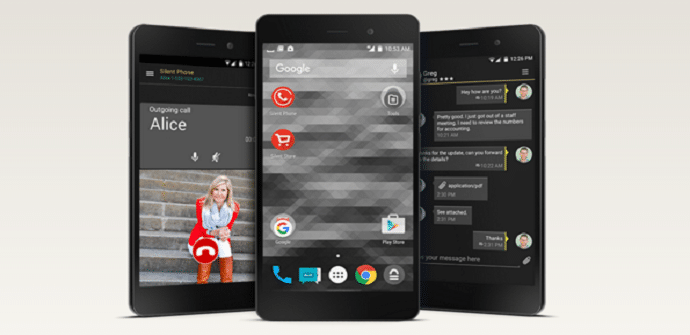
As in the case of Oxygen, Cyanogen and Flyme, SilentOS also has its base on Android and it is another addition to the popular operating system that tries to reinforce the fullfilment of security requirements of the terminals in which it is present, unlike the previous ones, based on an optimization of the devices and, especially, on a greater customization capacity.
Sober design
When we have talked about other software, we have highlighted points such as a greater selection of themes to customize the icons, backgrounds in which the color makes the use of the terminals more attractive and an intuitive handling that improves the accessibility of the terminals. In the case of Silent we meet some very basic funds that, despite being dark and looking somewhat dull, they do turn out to be elegant.

System created from scratch
Despite picking up Android elements such as open source and the possibility of modifying some aspects to some extent, Silent OS It has been conceived as a software in which security is the base and everything revolves around it. An example of this is the encryption of all communication made by users through devices equipped with this operating system. Despite having applications developed by Google as well as its catalog and its browser, Silent offers the possibility of using its own tools developed by the creators of this system, among which we highlight an alternative browser to Chrome or Firefox that is inspired by Tor.
Confidentiality as a strength
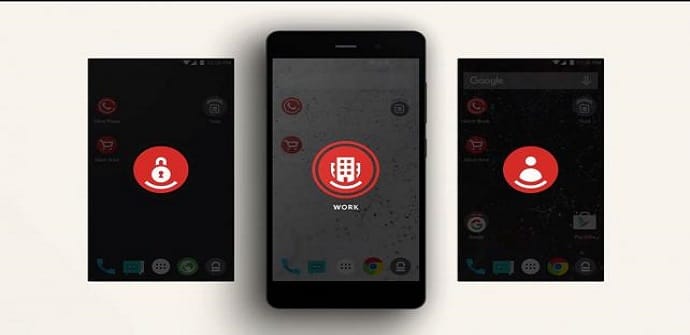
Although Silent has some very curious news such as a sensor that warns of the theft and loss of data and information, the privacy of users is another of the great strengths of this operating system. When downloading applications, we can manage the permissions that we grant to each one of them. On the other hand, and as we have commented when talking about black phone 2, we can create different screens for ourselves thanks to the Spaces option on the same device where we can organize what kind of content hub We save depending on whether it is business information, profiles on social networks or more personal content. On the other hand, the confidentiality agreement With which the main social networks or even Google, cannot know our location or send us advertising. Finally, the creation of private WiFi networks in open spaces that prevent the loss and theft of data when using wireless connections in public spaces.

Who uses Silent?
When talking about the Blackphone 2, we comment that its implantation is somewhat reduced Because it is a device aimed at people with high purchasing power in the business environment. However, according to Forbes magazine, more than 40 governments, with their armies and some of the most influential businessmen on the planet, whose identity is confidential, are users of one of these versions of the operating system, developed by Silent Circle.
An effective system?
The developers of Silent OS They have shown that it is possible to create software that is based on other existing ones and that guarantees the maximum security and privacy of the users without having to reduce other characteristics and functions of the operating systems. However, there are aspects that can disappoint some users, such as the need to give permission when sharing any photo or message.
Its greatest weakness: Its implantation
Silent developers agree that there is still a lot of work to be done, since the existence of brands that present their own software makes it difficult to expand and consolidate this operating system among the general public. The fact that it is currently present in a small number of high-end terminals also makes it difficult to implement.
After meeting a new member of the Android family and seeing that it is possible to maintain good security on our devices, do you think that Silent can be the solution to all the gaps that constantly appear on devices that use Android or yet there are still many aspects to improve that this software is not able to solve either? You have more information available such as lists of applications that will help to better protect your tablets or smartphones.